-
Why Grant Thornton
Whether you’re growing in one market or many, looking to operate more effectively, managing risk and regulation, or realising stakeholder value, our firms can help.
-
Culture and experience
Grant Thornton’s culture is one of our most valuable assets and has steered us in the right direction for more than 100 years.
-
Global scale and capability
Beyond global scale, we embrace what makes each market unique, local understanding on a global scale.
-
Join our network
In a world that wants more options for high quality services, we differentiate in the market to grow sustainably in today’s rapidly changing environment.
-
Leadership governance and quality
Grant Thornton International Ltd acts as the coordinating entity for member firms in the network with a focus on areas such as strategy, risk, quality monitoring and brand.
-
Africa
24 member firms supporting your business.
-
Americas
31 member firms, covering 44 markets and over 20,000 people.
-
Asia-Pacific
19 member firms with nearly 25,000 people to support you.
-
Europe
53 member firms supporting your business.
-
Middle East
8 member firms supporting your business.
-
Business consulting services
Our business consulting services can help you improve your operational performance and productivity, adding value throughout your growth life cycle.
-
Business process solutions
We can help you identify, understand and manage potential risks to safeguard your business and comply with regulatory requirements.
-
Business risk services
The relationship between a company and its auditor has changed. Organisations must understand and manage risk and seek an appropriate balance between risk and opportunities.
-
Cybersecurity
As organisations become increasingly dependent on digital technology, the opportunities for cyber criminals continue to grow.
-
Forensic services
At Grant Thornton, we have a wealth of knowledge in forensic services and can support you with issues such as dispute resolution, fraud and insurance claims.
-
Mergers and acquisitions
We work with entrepreneurial businesses in the mid-market to help them assess the true commercial potential of their planned acquisition and understand how the purchase might serve their longer-term strategic goals.
-
Recovery and reorganisation
Workable solutions to maximise your value and deliver sustainable recovery.
-
Transactional advisory services
We can support you throughout the transaction process – helping achieve the best possible outcome at the point of the transaction and in the longer term.
-
Valuations
We provide a wide range of services to recovery and reorganisation professionals, companies and their stakeholders.
-
Sustainability advisory
We can assist you with a variety of sustainability advice depending on your needs, ranging from initial strategy development, reporting and compliance support, through to carbon measurement and management.

-
IFRS
At Grant Thornton, our IFRS advisers can help you navigate the complexity of financial reporting from IFRS 1 to IFRS 17 and IAS 1 to IAS 41.
-
Audit quality monitoring
Having a robust process of quality control is one of the most effective ways to guarantee we deliver high-quality services to our clients.
-
Global audit technology
Our global assurance technology platform provides the ability to conduct client acceptance, consultations and all assurance and other attestation engagements.
-
Sustainability assurance
Our sustainability assurance services are based on our global network of specialists, helping you make more efficient decisions for the good of your organisation.

-
Corporate and business tax
Our trusted teams can prepare corporate tax files and ruling requests, support you with deferrals, accounting procedures and legitimate tax benefits.
-
Direct international tax
Our teams have in-depth knowledge of the relationship between domestic and international tax laws.
-
Global mobility services
Through our global organisation of member firms, we support both companies and individuals, providing insightful solutions to minimise the tax burden for both parties.
-
Indirect international tax
Using our finely tuned local knowledge, teams from our global organisation of member firms help you understand and comply with often complex and time-consuming regulations.
-
Transfer pricing
The laws surrounding transfer pricing are becoming ever more complex, as tax affairs of multinational companies are facing scrutiny from media, regulators and the public
-
Africa tax desk
A differentiating solution adapted to the context of your investments in Africa.
-
Sustainability tax
Through our sustainability tax advisory services, we can advise how environmental taxes, incentives, and obligations can impact your progress, requiring alignment with governmental and legislative pressures.

-
 Banking Holding banking to account: the real diversity and inclusion pictureWe explore how the banking sector can continue to attract, retain and nurture women to build a more diverse and inclusive future.
Banking Holding banking to account: the real diversity and inclusion pictureWe explore how the banking sector can continue to attract, retain and nurture women to build a more diverse and inclusive future. -
 Sustainability From voluntary to mandatory ESG: How banks can future-proof their operationsAs we move from voluntary ESG initiatives to mandatory legislation, we explore what the banking sector needs to prioritise.
Sustainability From voluntary to mandatory ESG: How banks can future-proof their operationsAs we move from voluntary ESG initiatives to mandatory legislation, we explore what the banking sector needs to prioritise. -
 IFRS IFRS 9 - Audit of Expected Credit LossesGPPC releases The Auditor’s response to the risks of material misstatement posed by estimates of expected credit losses under IFRS 9
IFRS IFRS 9 - Audit of Expected Credit LossesGPPC releases The Auditor’s response to the risks of material misstatement posed by estimates of expected credit losses under IFRS 9 -
 growthiQ Steering your company to long-term successHistory has something important to tell us about the difficulties of steering a business to long-term success – through seismic shifts in technology, consumer demands and product development. With that in mind it’s unsurprising that over half the world’s largest companies in the early 1900s had shut their doors by the late 1990s. Some, however, have endured.
growthiQ Steering your company to long-term successHistory has something important to tell us about the difficulties of steering a business to long-term success – through seismic shifts in technology, consumer demands and product development. With that in mind it’s unsurprising that over half the world’s largest companies in the early 1900s had shut their doors by the late 1990s. Some, however, have endured.
-
 International Financial Reporting Standards Implementation of IFRS 17 ‘Insurance Contracts’The auditor’s response to the risks of material misstatement arising from estimates made in applying IFRS 17 ‘Insurance Contracts’
International Financial Reporting Standards Implementation of IFRS 17 ‘Insurance Contracts’The auditor’s response to the risks of material misstatement arising from estimates made in applying IFRS 17 ‘Insurance Contracts’ -
 IFRS Get ready for IFRS 17After twenty years of development the IASB has published IFRS 17 ‘Insurance Contracts’, find out more.
IFRS Get ready for IFRS 17After twenty years of development the IASB has published IFRS 17 ‘Insurance Contracts’, find out more.
-
 Global business pulse - industry analysis Mid-market recovery spreads to more industriesThe index results for 13 key industries of the mid-market reveals a very uneven recovery from COVID-19
Global business pulse - industry analysis Mid-market recovery spreads to more industriesThe index results for 13 key industries of the mid-market reveals a very uneven recovery from COVID-19 -
 Global business pulse - industry analysis A very uneven recovery across industriesThe index results for 13 key industries of the mid-market reveals a very uneven recovery from COVID-19
Global business pulse - industry analysis A very uneven recovery across industriesThe index results for 13 key industries of the mid-market reveals a very uneven recovery from COVID-19 -
 Global business pulse - Sector analysis Clear patterns of damage from COVID-19 across the industriesThe index results for 12 key sectors of the mid-market reveal just how much or little the various parts of the economy were impacted by COVID-19.
Global business pulse - Sector analysis Clear patterns of damage from COVID-19 across the industriesThe index results for 12 key sectors of the mid-market reveal just how much or little the various parts of the economy were impacted by COVID-19. -
 Not for profit Mission: possible – putting impact at the heart of charityGlobal charitable continues to decline and charity leaders are increasingly looking at their own unique impact journey.
Not for profit Mission: possible – putting impact at the heart of charityGlobal charitable continues to decline and charity leaders are increasingly looking at their own unique impact journey.
-
 Access to finance Raise finance to invest in changePrepare your business to raise finance to invest in change.
Access to finance Raise finance to invest in changePrepare your business to raise finance to invest in change. -
 Private equity firms Private equity in the mid-market: reshaping strategies for 2021When the global COVID-19 pandemic stormed across the globe in early 2020, the private equity sector was hit hard but deals are coming back to the market.
Private equity firms Private equity in the mid-market: reshaping strategies for 2021When the global COVID-19 pandemic stormed across the globe in early 2020, the private equity sector was hit hard but deals are coming back to the market. -
 Mid-market businesses Getting ready for private equity investmentOur specialists explore how private equity firms are now working with their portfolios and how the mid-market can benefit from investment.
Mid-market businesses Getting ready for private equity investmentOur specialists explore how private equity firms are now working with their portfolios and how the mid-market can benefit from investment. -
 Mid-market businesses Myth-busting private equityNervous about partnering with Private Equity? We explore some of the common myths we come across when speaking to mid-market businesses about PE investment.
Mid-market businesses Myth-busting private equityNervous about partnering with Private Equity? We explore some of the common myths we come across when speaking to mid-market businesses about PE investment.
-
 Public sector Helping build the government of tomorrow, todayLearn about the Grant Thornton US public sector team.
Public sector Helping build the government of tomorrow, todayLearn about the Grant Thornton US public sector team. -
 Global business pulse - industry analysis Mid-market recovery spreads to more industriesThe index results for 13 key industries of the mid-market reveals a very uneven recovery from COVID-19
Global business pulse - industry analysis Mid-market recovery spreads to more industriesThe index results for 13 key industries of the mid-market reveals a very uneven recovery from COVID-19 -
 Global business pulse - industry analysis A very uneven recovery across industriesThe index results for 13 key industries of the mid-market reveals a very uneven recovery from COVID-19
Global business pulse - industry analysis A very uneven recovery across industriesThe index results for 13 key industries of the mid-market reveals a very uneven recovery from COVID-19 -
 Global business pulse - Sector analysis Clear patterns of damage from COVID-19 across the industriesThe index results for 12 key sectors of the mid-market reveal just how much or little the various parts of the economy were impacted by COVID-19.
Global business pulse - Sector analysis Clear patterns of damage from COVID-19 across the industriesThe index results for 12 key sectors of the mid-market reveal just how much or little the various parts of the economy were impacted by COVID-19.
-
 Industries European Real Estate PodcastJessica Patel, Tax Partner at Grant Thornton UK speaks with tax partners and directors across the network to share their insights on the real estate market and some of the challenges.
Industries European Real Estate PodcastJessica Patel, Tax Partner at Grant Thornton UK speaks with tax partners and directors across the network to share their insights on the real estate market and some of the challenges. -
 Industries European Real Estate PodcastJessica Patel, Tax Partner at Grant Thornton UK speaks with tax partners and directors across the network to share their insights on the real estate market and some of the challenges.
Industries European Real Estate PodcastJessica Patel, Tax Partner at Grant Thornton UK speaks with tax partners and directors across the network to share their insights on the real estate market and some of the challenges. -
 Global business pulse - industry analysis Mid-market recovery spreads to more industriesThe index results for 13 key industries of the mid-market reveals a very uneven recovery from COVID-19
Global business pulse - industry analysis Mid-market recovery spreads to more industriesThe index results for 13 key industries of the mid-market reveals a very uneven recovery from COVID-19 -
 Global business pulse - industry analysis A very uneven recovery across industriesThe index results for 13 key industries of the mid-market reveals a very uneven recovery from COVID-19
Global business pulse - industry analysis A very uneven recovery across industriesThe index results for 13 key industries of the mid-market reveals a very uneven recovery from COVID-19
-

-
 Global business pulse - industry analysis Mid-market recovery spreads to more industriesThe index results for 13 key industries of the mid-market reveals a very uneven recovery from COVID-19
Global business pulse - industry analysis Mid-market recovery spreads to more industriesThe index results for 13 key industries of the mid-market reveals a very uneven recovery from COVID-19 -
 Global business pulse - industry analysis A very uneven recovery across industriesThe index results for 13 key industries of the mid-market reveals a very uneven recovery from COVID-19
Global business pulse - industry analysis A very uneven recovery across industriesThe index results for 13 key industries of the mid-market reveals a very uneven recovery from COVID-19 -
 Retail How retail is positioning for successCOVID-19 provided some hard lessons for the retail industry. It is time to turn those into sustainable and well executed growth strategies in 2021.
Retail How retail is positioning for successCOVID-19 provided some hard lessons for the retail industry. It is time to turn those into sustainable and well executed growth strategies in 2021.
-
 Technology Mid-market tech companies lead the way on diversity and inclusionWe explore how the mid-market tech sector can continue to build and nurture a culture that’s increasingly more diverse and inclusive for women.
Technology Mid-market tech companies lead the way on diversity and inclusionWe explore how the mid-market tech sector can continue to build and nurture a culture that’s increasingly more diverse and inclusive for women. -
 Tax Resetting global tax rules after the pandemicBusinesses are seeing rising challenges, and finance heads are dealing with a range of new measures. To say the next 12 months are critical for businesses is an understatement.
Tax Resetting global tax rules after the pandemicBusinesses are seeing rising challenges, and finance heads are dealing with a range of new measures. To say the next 12 months are critical for businesses is an understatement. -
 TECHNOLOGY International tax reform: the potential impact on the technology industryIn this article, we’ve summarised key elements of the global tax reform proposals, their potential impact on technology industry and advice from our digital tax specialists on what technology companies can do to prepare.
TECHNOLOGY International tax reform: the potential impact on the technology industryIn this article, we’ve summarised key elements of the global tax reform proposals, their potential impact on technology industry and advice from our digital tax specialists on what technology companies can do to prepare. -
 TMT TMT industry: Fully charged or on standby?Our research revealed five key trends that resonated with Technology, Media and Telecoms (TMT) industry leaders around the world. We asked a panel of our experts from UK, US, India Ireland and Germany, to give us their reaction to the findings.
TMT TMT industry: Fully charged or on standby?Our research revealed five key trends that resonated with Technology, Media and Telecoms (TMT) industry leaders around the world. We asked a panel of our experts from UK, US, India Ireland and Germany, to give us their reaction to the findings.
-
 TMT TMT industry: Fully charged or on standby?Our research revealed five key trends that resonated with Technology, Media and Telecoms (TMT) industry leaders around the world. We asked a panel of our experts from UK, US, India Ireland and Germany, to give us their reaction to the findings.
TMT TMT industry: Fully charged or on standby?Our research revealed five key trends that resonated with Technology, Media and Telecoms (TMT) industry leaders around the world. We asked a panel of our experts from UK, US, India Ireland and Germany, to give us their reaction to the findings. -
 Cybersecurity One size fits nothingTechnology companies must adopt a new approach to digital risk: those that successfully develop a reputation for digital trust by demonstrating an unwavering commitment to cyber security and data privacy will be able to carve out a competitive advantage.
Cybersecurity One size fits nothingTechnology companies must adopt a new approach to digital risk: those that successfully develop a reputation for digital trust by demonstrating an unwavering commitment to cyber security and data privacy will be able to carve out a competitive advantage. -
 Technology, media & telecommunications Why it’s time for a 5G reality checkFigures suggest the mobile sector is maturing. While data usage continues to soar, mobile revenues are expected to flatten out over the next few years.
Technology, media & telecommunications Why it’s time for a 5G reality checkFigures suggest the mobile sector is maturing. While data usage continues to soar, mobile revenues are expected to flatten out over the next few years. -
 GrowthiQ Is blockchain right for your business?Blockchain has been seized upon by the financial services sector, where it is playing a crucial role in tracking and authenticating transactions.
GrowthiQ Is blockchain right for your business?Blockchain has been seized upon by the financial services sector, where it is playing a crucial role in tracking and authenticating transactions.
-
 International business Mid-market businesses lifted by rising tide of optimismOptimism among global mid-market business leaders rose to 67% in the first half of this year and they are markedly more optimistic about their prospects with global optimism having increased by 8%.
International business Mid-market businesses lifted by rising tide of optimismOptimism among global mid-market business leaders rose to 67% in the first half of this year and they are markedly more optimistic about their prospects with global optimism having increased by 8%. -
 Global business pulse - industry analysis Mid-market recovery spreads to more industriesThe index results for 13 key industries of the mid-market reveals a very uneven recovery from COVID-19
Global business pulse - industry analysis Mid-market recovery spreads to more industriesThe index results for 13 key industries of the mid-market reveals a very uneven recovery from COVID-19 -
 Hotels COVID-19: Checking in with the hotel industry one year onCOVID-19 provided some hard lessons for the hotel sector. It is time to turn those into sustainable and well executed growth strategies.
Hotels COVID-19: Checking in with the hotel industry one year onCOVID-19 provided some hard lessons for the hotel sector. It is time to turn those into sustainable and well executed growth strategies. -
 Global business pulse - industry analysis A very uneven recovery across industriesThe index results for 13 key industries of the mid-market reveals a very uneven recovery from COVID-19
Global business pulse - industry analysis A very uneven recovery across industriesThe index results for 13 key industries of the mid-market reveals a very uneven recovery from COVID-19
- By topic
-
Women in Business 2025
For 21 years, the Women in Business report has tracked the proportion of women in senior roles in the mid-market. Progress has been made but with gender equity over 25 years away, that isn’t soon enough.
-
The journey to a sustainable future
The world needs a sustainable mid-market. It’s vital to economies, societies and the planet. Businesses, governments, and other stakeholders must work collaboratively to make sure this vital part of the world economy succeeds.
-
Navigating tariffs
Traditional global export markets continue to shift as tariffs are introduced, presenting a challenge for mid-market firms
-
International business: Mid-market growth and expansion
The mid-market looks to international business opportunities for growth.
-
Women in Business 2025: Impacting the missed generation
The 2025 Women in Business report explores the external pressures and internal drivers that impact gender diversity in senior roles in the mid-market.
-
Women in tech: A pathway to gender balance in top tech roles
Grant Thornton’s 2024 Women in Business data suggests we are far from achieving parity within the mid-market technology sector.
-
Women in leadership: a pathway to better performance
What makes the benefits of gender parity compelling is the impact it can have on commercial performance.
-
Women in Business 2024
2024 marks the 20th year of Women in business where we monitor and measure the proportion of women occupying senior management roles around the world.
-
Women in business: Regional picture
We saw an increase in the percentage of senior management roles held by women, on a global level, but there are some significant regional and country variations.
-
Pathways to Parity: Leading the way
To push towards parity of senior management roles held by women, who leads within an organisation is vital.
-
Generating real change with a long-term focus
The most successful strategy to achieve parity of women in senior management is one which stands alone, independent of an ESG strategy.
-
People at the heart of great business
Businesses have started to put guidelines and incentives in place, focused on driving employees back to the office.
-
The journey to a sustainable future
The world needs a sustainable mid-market. It’s vital to economies, societies and the planet. Businesses, governments, and other stakeholders must work collaboratively to make sure this vital part of the world economy succeeds.
-
Ten considerations for preparing TCFD climate-related financial disclosures
Insights for organisations preparing to implement the International Sustainability Standards Board (ISSB)’s Standards.
-
COP28
COP28 was the first time there has been a global stocktake on progress against the Paris Agreement.
-
Transition Plan Taskforce publishes its final disclosure framework
As organisations in the private sector make commitments and plans to reach net zero, there's a growing need for stakeholders to be able to assess the credibility of their transition plans.
-
Promoting ESG excellence through tax
ESG considerations have never been more important for an organisation’s long-term success, but how can tax be used to add value to an ESG agenda?
-
International business: Mid-market growth and expansion
The mid-market looks to international business opportunities for growth.
-
Top five constraints to international business in the mid-market
Top five major constraints that are testing the mid-market’s ability to grow their businesses internationally.
-
Brand and international marketing – breaking global barriers
Brand has been identified as a key driver of mid-market success when looking to grow and develop international business.
-
The key to international business: Investing in people
How can recruitment and retention help grow international business?
-
Building resilience in international business
Evolving supply chains and trade patterns amid ongoing global uncertainty.
-
Example Financial Statements
The 2025 Interim Financial Statements provide general guidance on preparing interim financial statements in accordance with IFRS Accounting Standards.
-
IFRS 3
Mergers and acquisitions are becoming more common as entities aim to achieve their growth objectives. IFRS 3 ‘Business Combinations’ contains the requirements for these transactions.
-
IFRS 8
Our ‘Insights into IFRS 8’ series considers some key implementation issues and includes interpretational guidance in certain problematic areas.
-
IFRS 16
Are you ready for IFRS 16? This series of insights will help you prepare.
-
IAS 36
Insights into IAS 36 provides assistance for preparers of financial statements and help where confusion has been seen in practice.
-
IFRS 17
Explaining the key features of the Standard and providing insights into its application and impact.
-
Pillar 2
Key updates and support for the global implementation of Pillar 2.
-
Global expatriate tax guide
Growing businesses that send their greatest assets – their people – overseas to work can face certain tax burdens, our global guide highlights the common tax rates and issues.
-
International indirect tax guide
Navigating the global VAT, GST and sales tax landscape.
-
Global transfer pricing guide
Helping you easily find everything you need to know about the rules and regulations regarding transfer pricing and Country by Country reporting for every country you do business with.
Senior leaders have seen significant change in the past two years in how cyber incidents are affecting their businesses. With attacks becoming increasingly sophisticated, one of the biggest challenges for companies is to measure these often intangible impacts in real terms.
In this article we speak to Adam Schrock, managing director of cyber risk at Grant Thornton US, to understand the shifting cyber landscape and mitigate against future attacks.
The changing shape of cyber attacks
With technology ever changing, there are no physical boundaries as to where and when security breaches strike. Businesses should have a robust risk management strategy closely aligned to the wider business strategy regardless of their physical location. Adam recalls the WannaCry ransomware case in May 2017, which infected and encrypted data on over 200,000 computers throughout the world.
From the UK’s National Health Service to government bodies in India, Russia, and Romania, organisations across the globe suddenly found themselves unable to access their data. The ransomware also affected universities in Canada, Indonesia and China, and numerous businesses including Honda, DeutscheBahn and LATAM airlines.
As Adam explains, WannaCry was able take control of machines because users had not installed the necessary updates to protect against known vulnerabilities that the WannaCry malware exploited. He says, “WannaCry gives us the lesson to analyse and install critical security updates on computers and mobile devices because once the malware is inside an organisation, it spreads. It is about reacting quickly and limiting the damage. Of course, where possible, it’s far better to be prepared and prevent the breach in the first place.”
Beyond the numbers
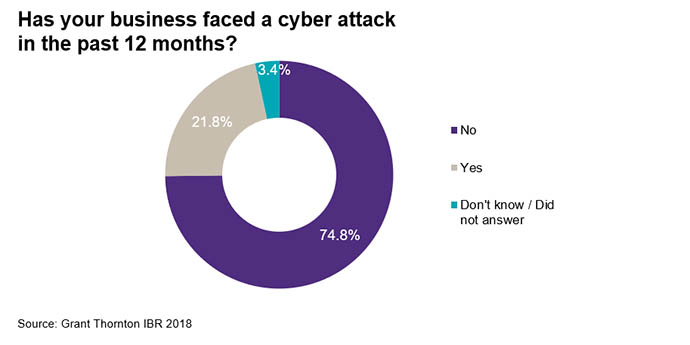
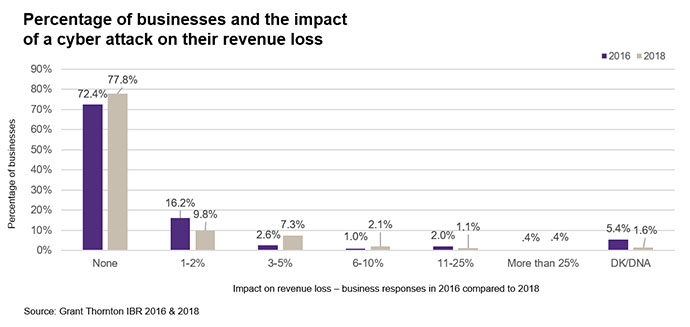
Reassuringly, the number of cyber attacks globally has not increased dramatically in the past year, though we have seen a 6.8% rise since 2015. Impact on revenue also appears stable, with businesses reporting either no loss or only a 1-2% decrease as a result of a cybersecurity breach.
However, these figures do not show us the entire picture, Adam says. “Although this increase seems low, and the general indication is the frequency of cyber incidents is stable, there is more to the story here.”
Front of mind for chief security officers and chief information officers is not only the number of cyber events affecting their businesses, but the exact impact of those breaches.
How have the impacts shifted?
The effects of cyber attacks on businesses over the past two years have significantly changed. In 2016[i], senior leaders ranked reputation loss as the most likely impact (29.2%), followed by management time (26%) and customer loss or churn (16.4%). However, senior leaders surveyed in 2018[ii] said the most likely impact had shifted to the drain on management’s time (29.9%), with reputational loss ranking second at 22.3%, and clean-up costs entering the top three position (18.4%). 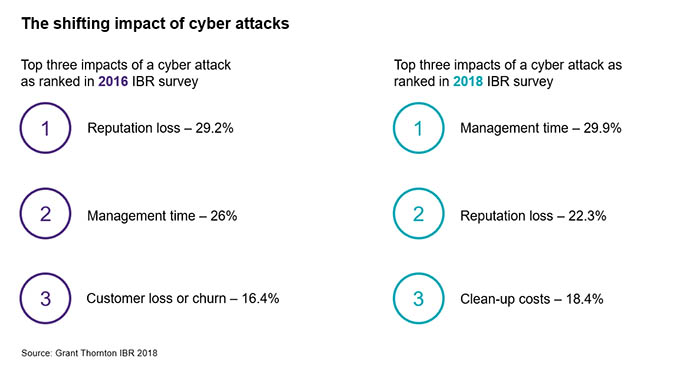
Adam sheds some light on these figures. “There’s a definite shift to the impact on board management time, technical clean-up costs and limiting the damage, be that PR, IT or otherwise.” There are many effects a cyber attack can have on a business and although the nature of a breach can vary by size and industry, there are some common themes.
“It’s important to remember that brand names and reputations are at stake immediately following an attack,” Adam says. “But for big brands, even big breaches can have a small impact in the long term.”
Home Depot is a good example – an established company with strength and infrastructure that experienced a lot of public damage following its 2014 data breach. Yet this NYSE listed company has a long-term upward trend. Despite the bumpy year or two following the data breach in 2014, Home Depot’s stock price has risen from the low US$80s in January 2014 to now fluctuating around the US$180 mark[iii]. The size of the company and its long-term growth trajectory can determine its ability to recover from an attack.
Quantifying the impact
“Ways a business can easily measure tangible impacts are by calculating the cost per record or per event.” Adam advises. “You can assign a cost of notifying people of the breach or issue you have experienced and depending on the number of customers or business partners affected, you will have a sum of the impact.”
Direct loss of sales due to the closure of a business, even for a few hours, can be calculated. Losses as a result of temporary suspension of a website, phone system or mobile app are easily discovered due to lost efficiency and being unable to take sales or enquiries. Another hard cost comes from regulatory fines.
Unfortunately, some outcomes can be less tangible, such as reputation loss or longer-term impact on revenue that is directly attributable to the attack – and the latter are much harder to assign a monetary value. Another challenge of quantifying the impact of an attack is acknowledging there is an opportunity cost of human and technical resources being taken off other projects to deal with the breach.
Other measures taken in the ‘clean-up’ may be hard to quantify, such as revenue. It is also hard to estimate loss of sales or future business as a direct result of a specific event, further complicated by any additional attacks or unrelated breaches of security.
Adam says, “What senior leaders would find useful is an effective way to measure the financial impact on a business – and this comes back to tangible and intangible measures. Brand names and reputations are at stake immediately following a cyber attack but reputation loss and integrity loss are hard to quantify.”
What action are governments taking to combat cyber attacks?
Depending on the industry and regulation environment, some governments and regulators are proactively addressing changes in the security landscape. Last August, the New York Department of Financial Services (DFS) announced[iv] a new cybersecurity regulation which requires registered financial services institutions to protect data with a cybersecurity program and to report breaches via the DFS online portal.
“Accountability is key – there needs to be a person/owner internally, be they a contractor for a specific project or a permanent staff for ongoing assessments,” Adam explains.
In Europe, the General Data Protection Regulation (GDPR) came into force on 25 May, which applies to both businesses located in the European Union (EU) and those that trade with the EU. The regulation is designed to better protect individuals and there are significant penalties for non-compliance.
Renan Piamonte, audit partner and head of risk management at Grant Thornton Philippines, adds another perspective. “As an economic bloc, the EU is in the Philippines’ top three largest trading partners for goods and services, even bigger than the United States.”
“The good news is that companies complying with the Philippines’ Data Privacy Act of 2012 have a very good chance of being ready for the GDPR, since this Act is largely based on international data privacy frameworks,” says Renan.
So, on the plus side, businesses will benefit from regulatory changes because they present an opportunity to thoroughly understand what data they hold and how to use it more effectively.
“In our experience, clients and companies in general are positive about the changes resulting from regulations such as the GDPR and have a comfort level in know they are doing the right thing,” Adam adds.
How can you protect your business from a cyber attack?
Senior leaders have different attitudes to risk depending on industry, sector and even personality type. “It is important to realise that a business can never be 100% secure,” Adam says, “and it really depends on your risk tolerance level.”
“A business can always do more to protect and prevent against risks and this is where we can help. We guide our clients on which regulations are relevant to their business and assess where they are on their maturity path. We also compare against their peers in their industry. Many clients find this valuable because we ask them where they want to be on the risk tolerance spectrum and where necessary, we help them achieve their desired security posture.”
Properly embedding cybersecurity management into existing business processes can also have huge benefits. This integration ensures that an holistic view is taken on business risks.
“We also help new CISO and CSOs when they start a new role in a business. We recommend they look at their security strategy, at regulatory compliance, and take a risk-based approach overall. Our clients like that Grant Thornton are proactive in assessing their situation. We look at gaps in their control framework and help CISOs plan for the next 3-5 year timeframe.”
What next?
If you would like to discuss your cybersecurity risk management or would like us to do an assessment of your security and control maturity level, contact one of our Grant Thornton member firms in your region.
[i] Source: Grant Thornton IBR Q3 2016
[ii] Source: Grant Thornton IBR Q1 2018
[iii] Source: Home Depot Product Authority, LLC, 2018
[iv] Source: Department of Finance Services, New York State, 2017